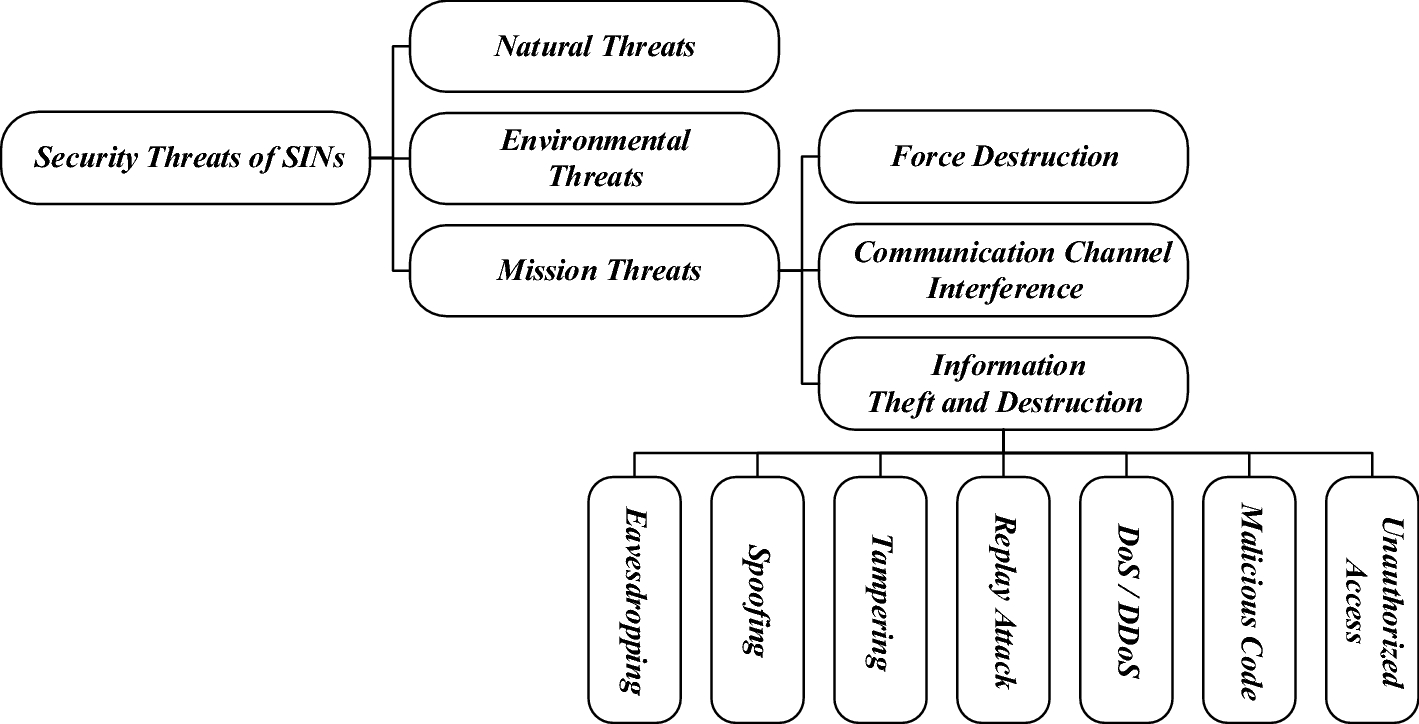
Survey on security issues of routing and anomaly detection for space information networks | Scientific Reports

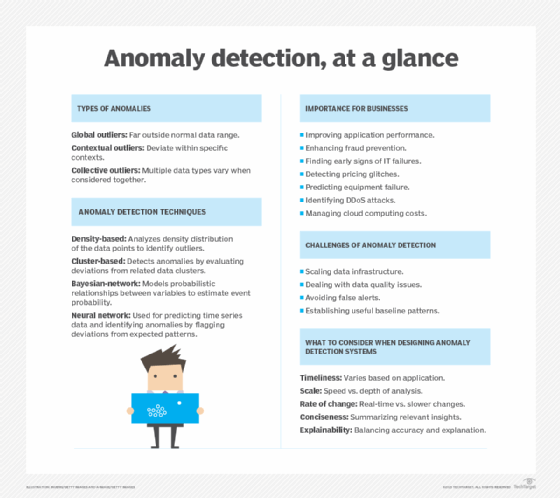
What Is Network Behavior Anomaly Detection? Definition, Importance, and Best Practices for 2022 - Spiceworks
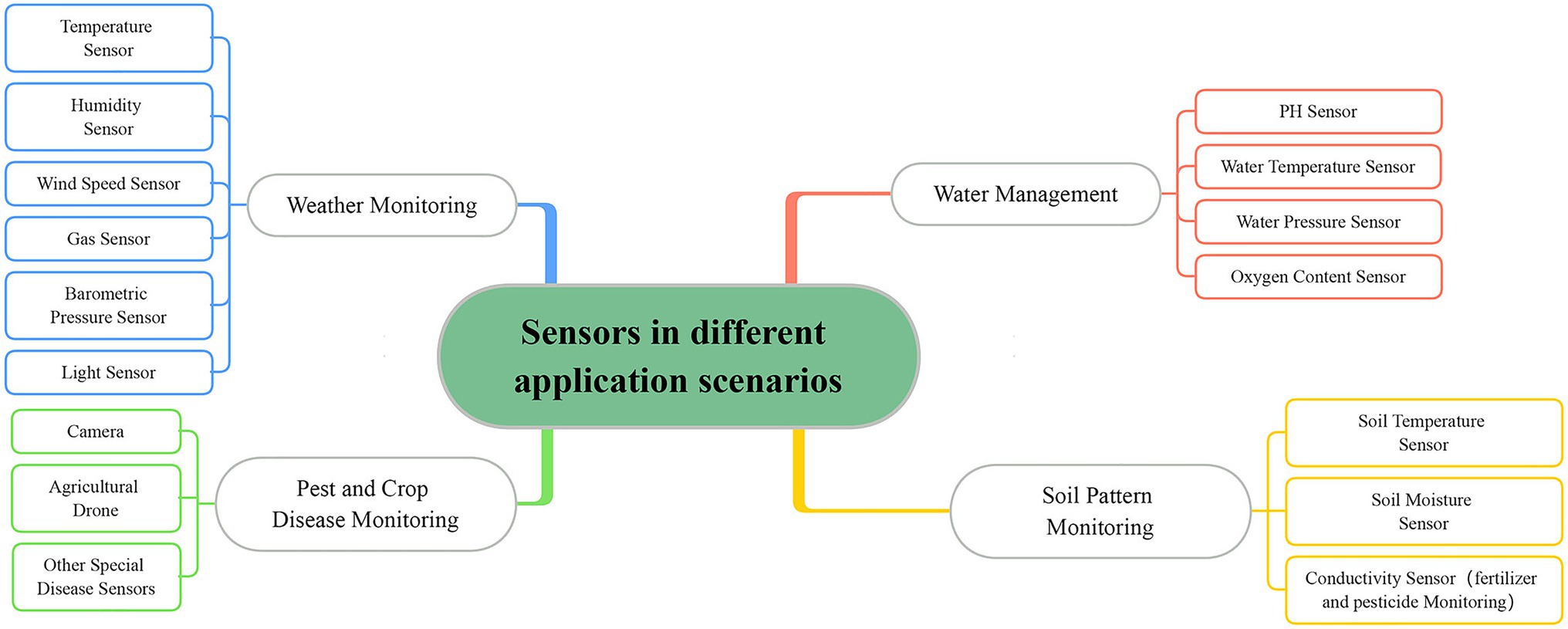
Frontiers | Anomaly Detection for Internet of Things Time Series Data Using Generative Adversarial Networks With Attention Mechanism in Smart Agriculture

Network Anomaly Detection System. (Red arrows represent control actions... | Download Scientific Diagram
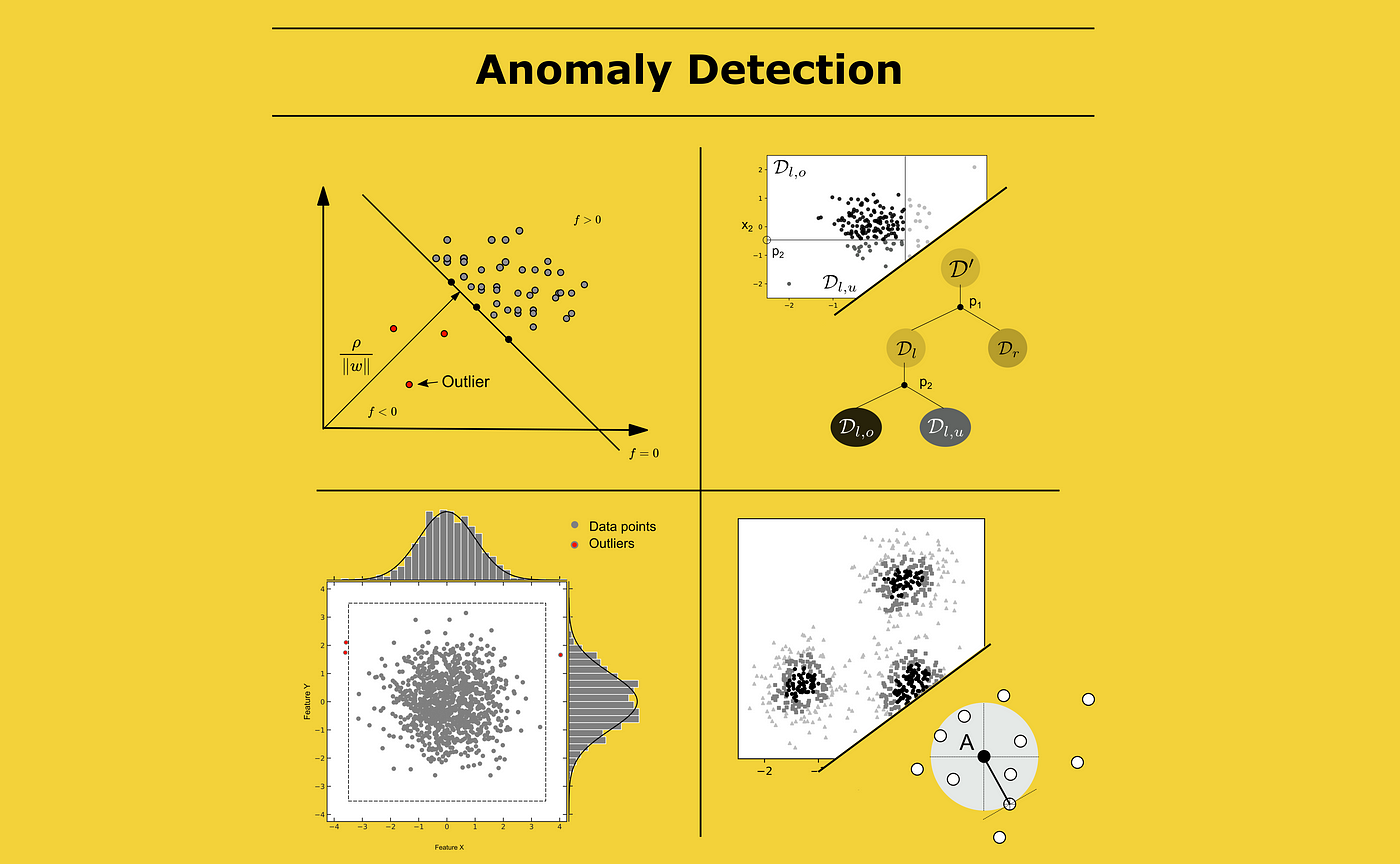
A Comprehensive Beginner's Guide to the Diverse Field of Anomaly Detection | by Dominik Polzer | Towards Data Science

What Is Network Behavior Anomaly Detection? Definition, Importance, and Best Practices for 2022 - Spiceworks
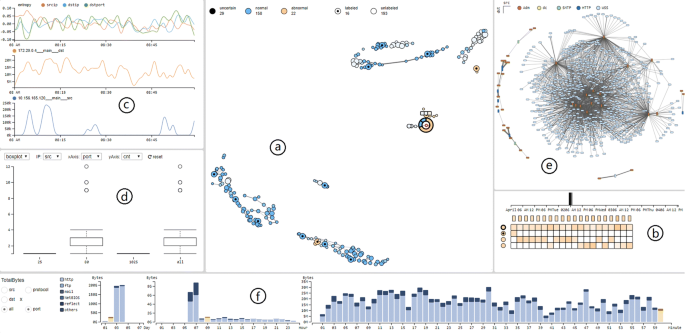
An interactive visual analytics approach for network anomaly detection through smart labeling | SpringerLink
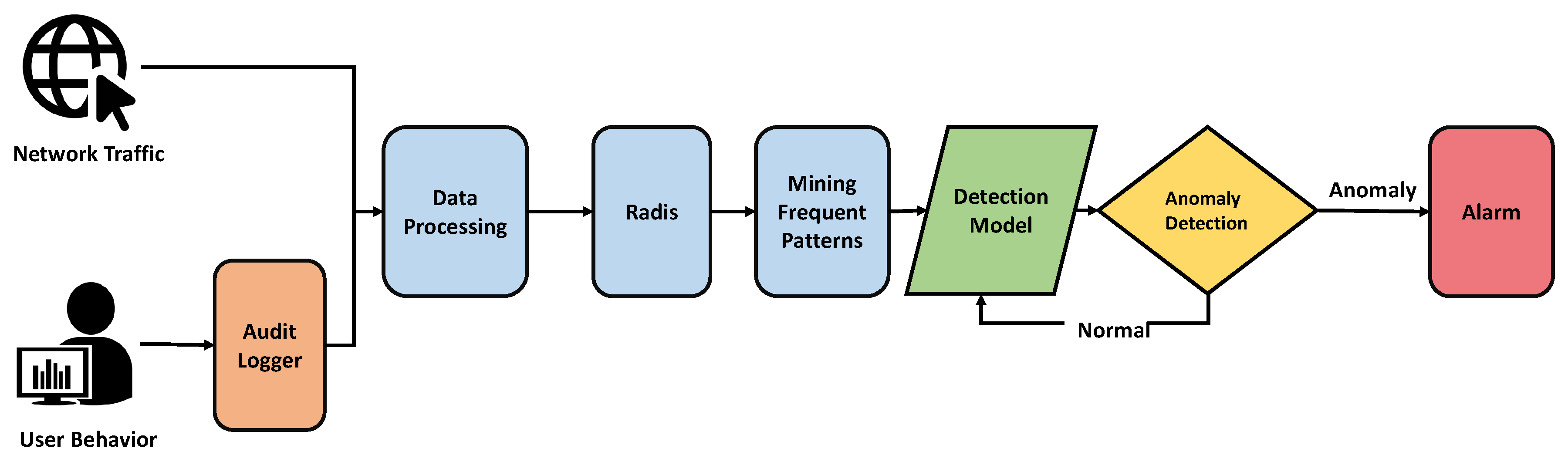
![PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e467ff1ea3a0c535a0cef87f7e0daa414d524d9d/7-Figure3-1.png)
![PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e467ff1ea3a0c535a0cef87f7e0daa414d524d9d/12-Figure8-1.png)

![PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e467ff1ea3a0c535a0cef87f7e0daa414d524d9d/20-Figure13-1.png)
![PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e467ff1ea3a0c535a0cef87f7e0daa414d524d9d/9-Figure4-1.png)


![Network intrusion detection using oversampling technique and machine learning algorithms [PeerJ] Network intrusion detection using oversampling technique and machine learning algorithms [PeerJ]](https://dfzljdn9uc3pi.cloudfront.net/2022/cs-820/1/fig-1-full.png)
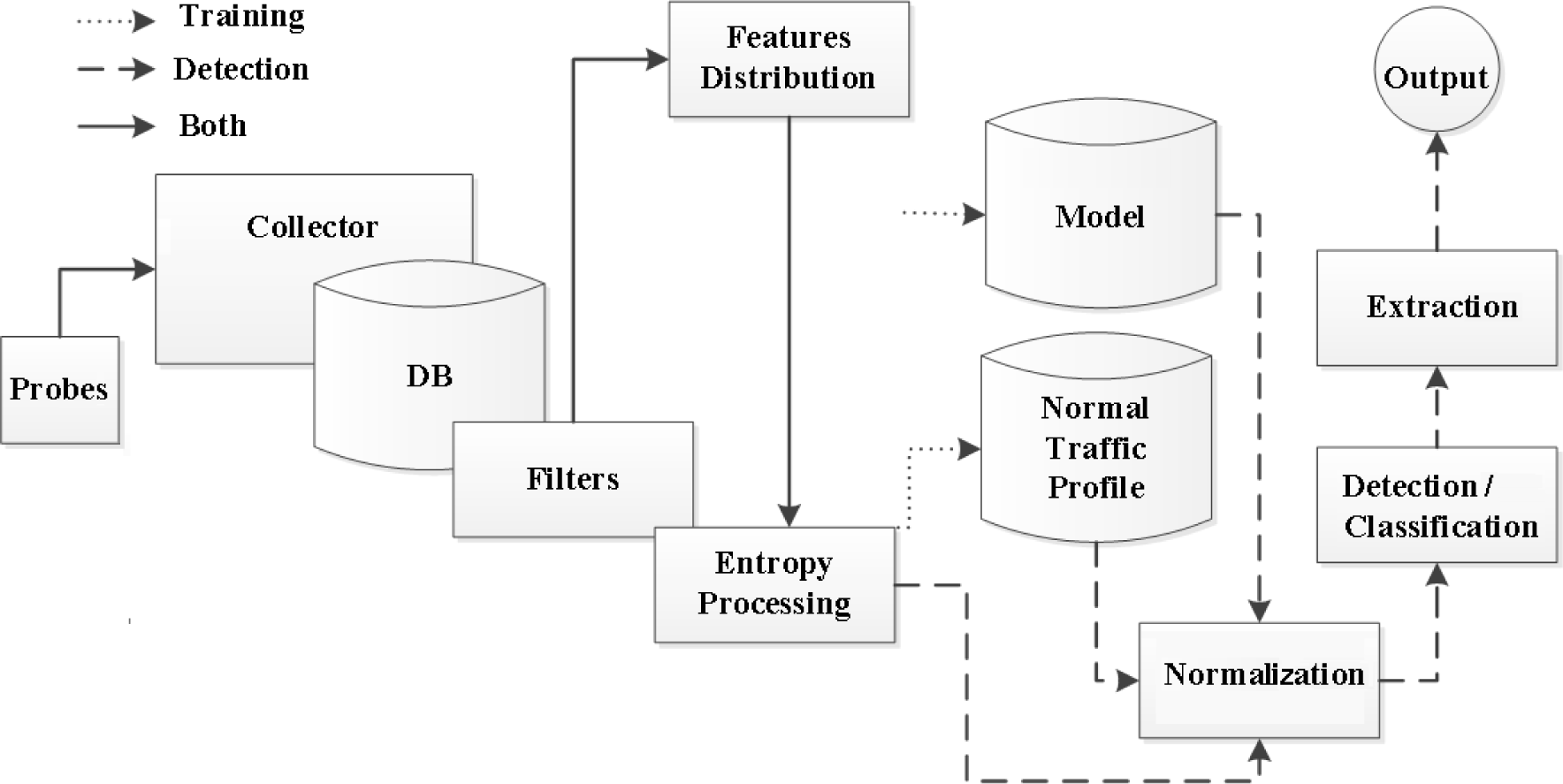
![PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar PDF] Network Anomaly Detection: Methods, Systems and Tools | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e467ff1ea3a0c535a0cef87f7e0daa414d524d9d/10-Figure6-1.png)
